During the Spring of 2025, a series of reports emerged of a campaign of scams, in which fraudsters have been impersonating trademark law firms and targeting brand owners with allegations of third-party attempts to register the brand name. In some cases, the fraudsters have been observed to create wholly fake organisations; in others, the names of legitimate firms have been used, in instances of brand impersonation (often with the use of a deceptive domain name similar to that of the real company).
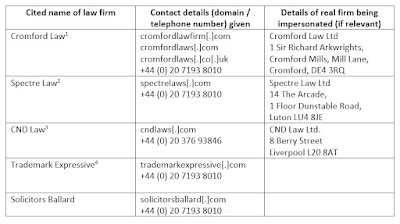
In one such set of scams, for example, a group of company names and associated contact details as shown in Table 1 were found to have been used. All of these examples have explicitly been reported as scams on the website of the Solicitors Regulation Authority[1,2,3,4].
Table 1: Company names and credentials used in identified trademark law-firm scams
Whilst there is no reason to suppose that all of these examples are necessarily connected to each other as a single coordinated campaign, there are certainly connections between at least some of the scam sites. For example, four of the five entities use the same (apparently London-based) telephone number. This might be indicative of nothing more than the use of a common website template being used across these scams, but if the telephone numbers are actively being used as means of contact in the campaigns, there is therefore a strong indication that at least these four are associated with the same underlying fraudsters.
These types of insights are key to the idea of clustering[5], which is a technique used in brand protection and other related areas of analysis, intended to establish links between infringements. An extension of this idea can also be combined with open-source intelligence ('OSINT') investigation techniques to identify other related examples.
For example, a simple search for the shared phone number referenced above shows that it has also been used in yet another law-firm scam ('Wozi Law Firm', wozilawfirm[.]org)[6], impersonating a legitimate company of the same name (wozilaw[.]com).
As of the date of analysis (08-May-2025), none of the scam websites in question were found to be live, although all were found previously to have been active for a sufficient length of time to have been indexed by Google. The associated abstracts provide some insights into the content which was formerly present (Figure 1), which can also serve as a basis for searches for other (potentially related) sites featuring similar content, or for further establishing similarities between the sites.
Figure 1: Example of the Google abstract for the scam site formerly present at cromfordlaws[.]com
In one of the above cases, a historical cached view of the site was available from the Archive.org website[7] (Figure 2).
Figure 2: Historical cached screenshots (from 24-Mar-2025) (courtesy of Archive.org) of the scam site formerly present at cromfordlawfirm[.]com
Carrying out a deeper analysis of the domains utilised in the various scams can also serve as a basis for establishing further clusters of associated examples. Table 2 shows the dates of registration, host-IP addresses, named registrants and registrars for the domains in question (for the most recent available whois records).
Table 2: Registration and configuration details for the domains utilised in the scams referenced above
It is also worth noting that, in some cases, the DomainTools website also possesses cached historical views of the sites in question (Figure 3).
Figure 3: Historical cached screenshot (from 13-Mar-2025) (courtesy of DomainTools) of the scam site formerly present at wozilawfirm[.]org
In cases where the registrant details are redacted (which is very common following the introduction of GDPR), information such as the identity of the privacy service provider does not serve as a very effective means of clustering together related results. However, the other details (as shown in Table 2) can be more diagnostic. It is particularly noteworthy that two of the IP addresses appear twice in the table which, whilst not definitive of a link between the co-hosted sites, can be a useful indicator if other commonalities are also present.
Reverse-IP-address look-ups reveal four further sites which are co-hosted with at least one of the examples shown in Table 2, also feature references to 'law' in the domain name, and show other characteristics such as registrar, name patterns and nearby registration dates in common (Table 3). It is highly likely that these comprise additional clusters of related scam sites and, whilst again none is currently active, a cached screenshot was again available in one case (Figure 4).
Table 3: Additional potential scam domains sharing hosting characteristics with one or more examples from Table 2
Figure 4: Historical cached screenshot (from 30-Apr-2025) (courtesy of DomainTools) of the scam site formerly present at cndlawfirms[.]com
It is also possible to extend these ideas to much broader domain searches. For example, zone-file analysis reveals that there are over 47,000 domains with named ending with (for example) 'lawfirm(s)'. Considering just the .org domains (to provide an easily manageable dataset, and by analogy with the wozilawfirm[.]org example identified previously) and focusing just on the domains registered through Hostinger, PDR, or Namecheap as registrar, since the start of 2025 (i.e. those most likely to be live and associated with the identified campaign(s)), we find 17 further candidate domains, of which seven resolve to additional live sites of potential concern. Two examples are shown in Figure 4 - both are registered via Hostinger Operations, UAB, hosted at the same IP address (34.120.137.41) and registered in a similar timeframe (on 19-Jan and 23-Jan respectively), and feature other suggestions of possible non-legitimacy (such as the use of placeholder content, webmail addresses, inconsistent contact details, etc.). The sites also have a broadly similar appearance, possibly suggestive of the use of a common website template.
Figure 4: Example of a 'mini-cluster' of two further sites of potential concern ('Nazakat' and 'Elite Law Firm')
The ideas presented in this article - namely the use of analysis and investigation techniques to connect infringements and identify additional related examples - are key to a highly significant area of brand protection analysis. These types of approaches can be used to provide early identification of sites which may pose a threat - potentially before they are utilised extensively and subsequently reported online - and can be built into the analysis and prioritisation approaches used for active monitoring services. This is also an area where AI-based analysis can provide a compelling addition to traditional analysis techniques, in the identification of key features from highly rich datasets.
References
[1] https://www.sra.org.uk/consumers/scam-alerts/2025/apr/cromford-law/
[2] https://www.sra.org.uk/consumers/scam-alerts/2025/apr/spectre-law/
[3] https://www.sra.org.uk/consumers/scam-alerts/2025/may/cnd-law-ltd-david-marks-nick-cross/
[4] https://www.sra.org.uk/consumers/scam-alerts/2025/mar/ballard-and-trademark-expressive/
[6] https://regulationandcomplianceoffice.co.uk/raco-roundup-9/
[7] https://web.archive.org/web/20250324145542/https://www.cromfordlawfirm.com/
This article was first published on 3 June 2025 at:











No comments:
Post a Comment